SUNY New Paltz is in the process of adding Two-Factor Authentication (2FA) to their adminstrative computer systems, and I have been trying it out. This is a report on some of the things I’ve learned, such as how to get it to remember you for 5 days without having to accept all third-party cookies.
Two-Factor Authentication
A lot of people are familiar by now with Two-Factor Authentication. After you log in with a password (something you know) a message of some sort is communicated to you through a secure channel to a device assumed to be under your control (something you have). You then have to prove that you received this message, to prove that it is really you logging in, not just someone who has stolen your password.
A very familiar example is 2FA on Google accounts. When you log in with your password, Google sends a 6-digit code number as a text message to your mobile phone. (They will also call you on a voice land-line, if you don’t have a way to receive texts.) You then type in that 6-digit number to complete the authentication process. Facebook does something similar, but you use the Facebook app on your mobile device to get the 6-digit code, which changes every few minutes. I highly recommend enabling 2FA on both Google and Facebook.
New Paltz is using a 2FA system from Duo Security, which can work the same way, sending you a 6-digit “passcode” for you to enter as part of the authentication process. But Duo also offers the option of a “push,” in which the message is sent to an app on a device assumed to be under your control, and only your control. In that case you can simply push a button on the app to accept the authentication (or another button to deny it). You don’t have to type in the 6-digit number. The device can be a mobile phone, a “dongle” device you carry on your keychain, or even an Apple watch. Here is the challenge page you will see after you enter your password:
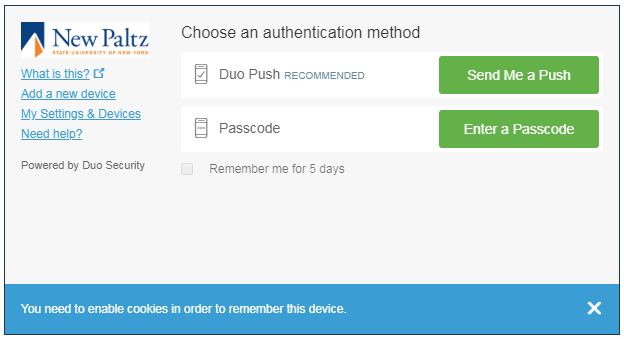
Click on “Send me a Push” and then press the “Accept” button on your mobile device and you are in. Easy.
Apple Watch
I have an Apple watch, which makes using Duo 2FA very easy.
After I’ve entered my password I click “Send me a Push,” and a screen on my watch comes up with the name of the site or service to which I’m trying to authenticate, and a button to Approve the connection (See Figure 2).
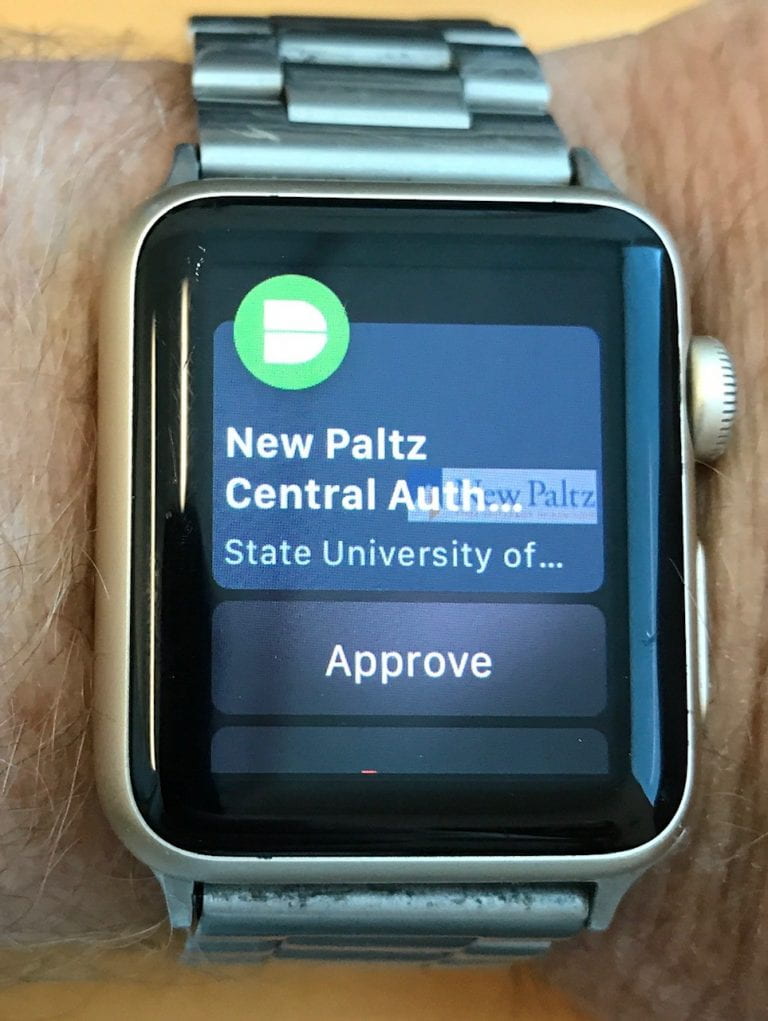
There is another option under that, to Deny the connection, but I have to scroll down for that option. So far I have not accidentally pressed Approve when trying to scroll down to get to Deny but it’s a concern.
I prefer using the watch for authentication, but I have learned that if I have recently been using my iPhone and it is still open then the “push” will go to the phone and will not go to the watch. That is confusing at first, when you expect the push on your watch and it does not show up there. Check your phone.
(Maybe they could make it show up on both the phone and watch?)
In order to use the Apple watch app I had to install the iPhone app first, and then open the Apple Watch controls and find the Duo app there and enable “Show App on Apple Watch”.
Third-Party Cookies
When you initiate authentication and the Duo challenge page comes up, there is the option to have the device remembered (and authorized) for 5 more days. You can see a checkbox for this in the Challenge page in Figure 1. You can also see the disclaimer that “You need to enable cookies in order to remember this device.” What they actually mean is that you need to enable third-party cookies, which are cookies set on your browser from a site other than the one you are visiting. Even if you have enabled cookies in your browser, you will find that you are unable to check that box if your browser does not allow third-party cookies.
By default, I turn off third-party cookies. They are used for tracking by advertisers, which I prefer to avoid, and I can’t help but think they are a potential security weakness, though as of this writing I don’t know of any active exploits. The compromise is that browsers let you make exceptions, blocking most third-party cookies but allowing them from selected sites. Using Chrome, I found I could enable this 5-day “remember me” feature and still block third-party cookies in general if I made this exception for the site:
[*.]duosecurity.com
The special characters at the beginning are a “wild-card” match pattern, which is necessary because the hostname part of the URL seems to change from session to session. (In contrast, when I found how to enable Starfish Early Alert with a single exception for third-party cookies the hostname was specific to our campus.) The same should work with Firefox.
Although I have not finished testing yet, it seems that authorization is based on IP address, which means that if you use Duo 2FA on your desktop computer using one browser, then you are automatically authorized using a different browser. Does this required checking the “remember me” box or is it automatic? I am still trying to figure that part out.
I couldn’t resist commenting. Exceptionally well written!
Take a look at my website: เครดิตฟรี50